Securely Connect to Amazon RDS using SSH Tunneling and Table Plus
Discover how to securely connect to an Amazon RDS instance without exposing it to the public. This guide walks you through SSH tunneling, setting up a bastion host, and ensuring optimal security practices.
Creating a tunnel connection to an Amazon RDS instance is a common way to securely connect to a database without exposing it to the public internet. This is typically done using SSH tunneling. Here's a step-by-step guide on how to set up a tunnel connection to an Amazon RDS instance:
Prerequisites:
- SSH Access: You need SSH access to an EC2 instance that has access to the RDS instance. This EC2 instance will act as a "jump host" or "bastion host".
- SSH Client: You need an SSH client installed on your local machine. For Linux and macOS, this is typically available by default. For Windows, you can use tools like PuTTY.
- Database Client: You need a database client on your local machine to connect to the RDS instance through the tunnel.
Steps:
Configure Security Groups:
- Ensure that the RDS instance's security group allows inbound connections from the EC2 instance (jump host).
- Ensure that the EC2 instance's security group allows inbound SSH connections from your local machine's IP address.
Establish an SSH Tunnel:
- Open a terminal or command prompt.
- Use the following command to establish an SSH tunnel
ssh -L local_port:rds_endpoint:rds_port ec2-user@ec2_instance_ip -i path_to_ec2_private_key local_port: A free port on your local machine (e.g.,8888).rds_endpoint: The endpoint of your RDS instance
(e.g.,mydb-instance.123456789012.us-west-1.rds.amazonaws.com).rds_port: The port on which your RDS instance is listening (e.g.,3306for MySQL).ec2_instance_ip: The public IP address of your EC2 instance.path_to_ec2_private_key: The path to the private key file for your EC2 instance (e.g.,~/path/to/my-key.pem).
Connect to RDS through the Tunnel:
- Now that the tunnel is established, you can use your database client to connect to the RDS instance as if it's running on
localhostat thelocal_portyou specified. - For example, if you're using MySQL, you can connect using
mysql -h 127.0.0.1 -P 8888 -u db_username -p - Using Table Plus:
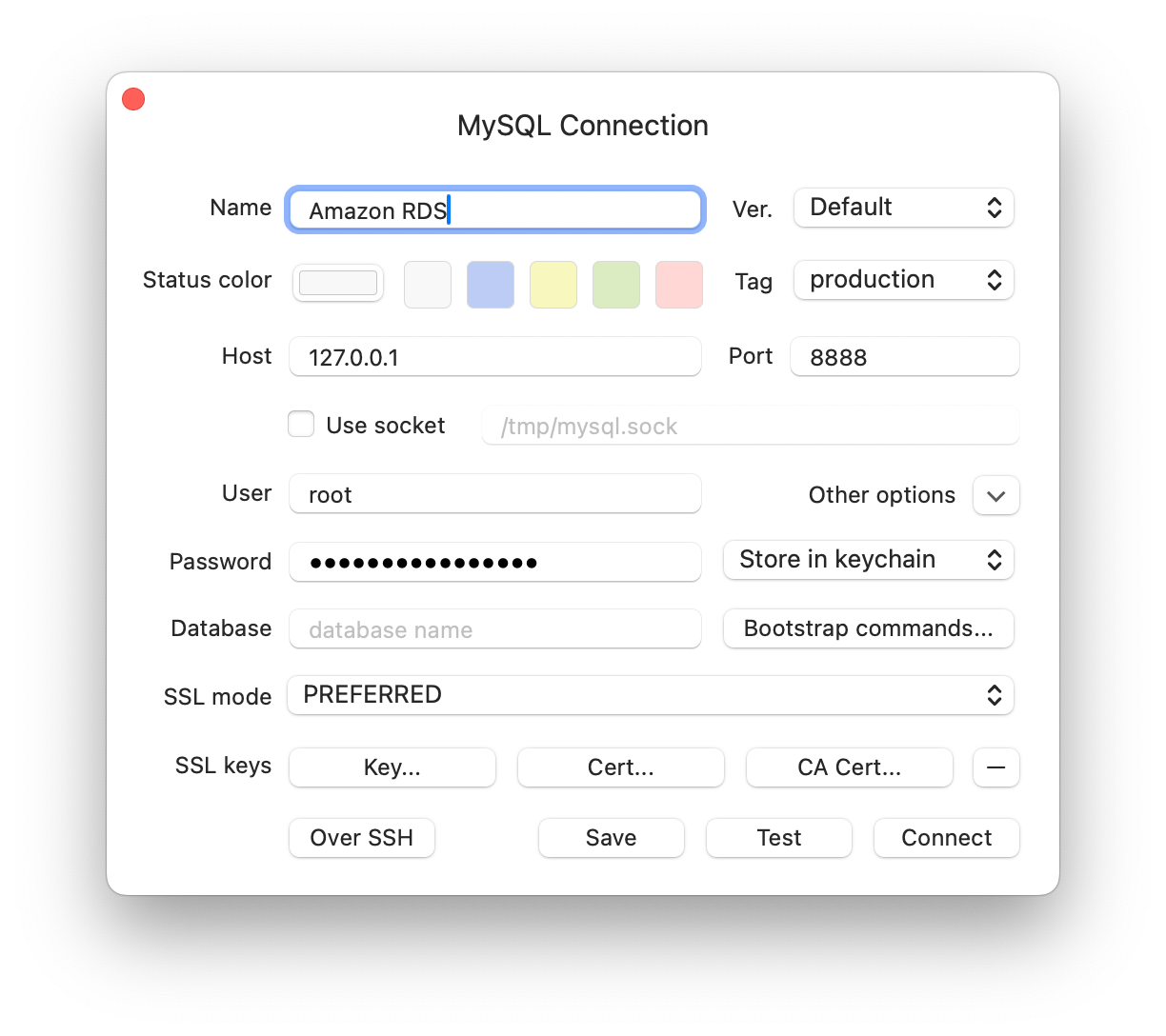
Close the Tunnel:
- Once you're done with your database tasks, you can close the tunnel by pressing
CTRL+Cin the terminal where the SSH tunnel is running.
Notes:
- Always ensure that your EC2 and RDS instances have strict security group rules to minimize security risks.
- Using a bastion host or jump host is a best practice to access resources in a private subnet, as it provides an additional layer of security.
